Looking back before 2020, we knew where the digital transformation was taking us. But we had no idea how quickly it would arrive. Because of the pandemic, our journey to cloud migration happened at light speed. As a result, businesses today are now less constrained by traditional network infrastructures and designated worksites, and their employees have the freedom to work wherever and whenever. And while we’ve always had some agility within our digital structures to move work between on-prem and remote, what we’re seeing now is a completely new category, a new age that I like to call the unbound enterprise.
Unbound Work Requires Unbound Security
Understanding the Need for the Unbound Enterprise
When COVID quickly forced a majority work from home environment, many companies experienced a surge in productivity and the wide-spread adoption of the cloud. For these companies, it is likely that leadership will keep remote work (in some form) as a long-term option for employees, even after the threat of the pandemic has passed. In fact, they’re embracing new, flexible technologies and arrangements that offer the ability to work from anywhere, at any time, on any device, and across applications that can exist anywhere. Users are no longer bound to the workplace. Applications and data are no longer bound to the corporate network. That’s what unbound means to me.
Getting to unbound depends on a corporate leadership open to the change of moving traditional software to the cloud. That is step one. Step two is re-envisioning cybersecurity for the unbound enterprise. As remote workers shift to cloud applications for productivity, and the workforce becomes more agile, traditional perimeter security breaks down. In this new environment, people can be anywhere. The data center is no longer the center of the data. User and data become the new security perimeter.
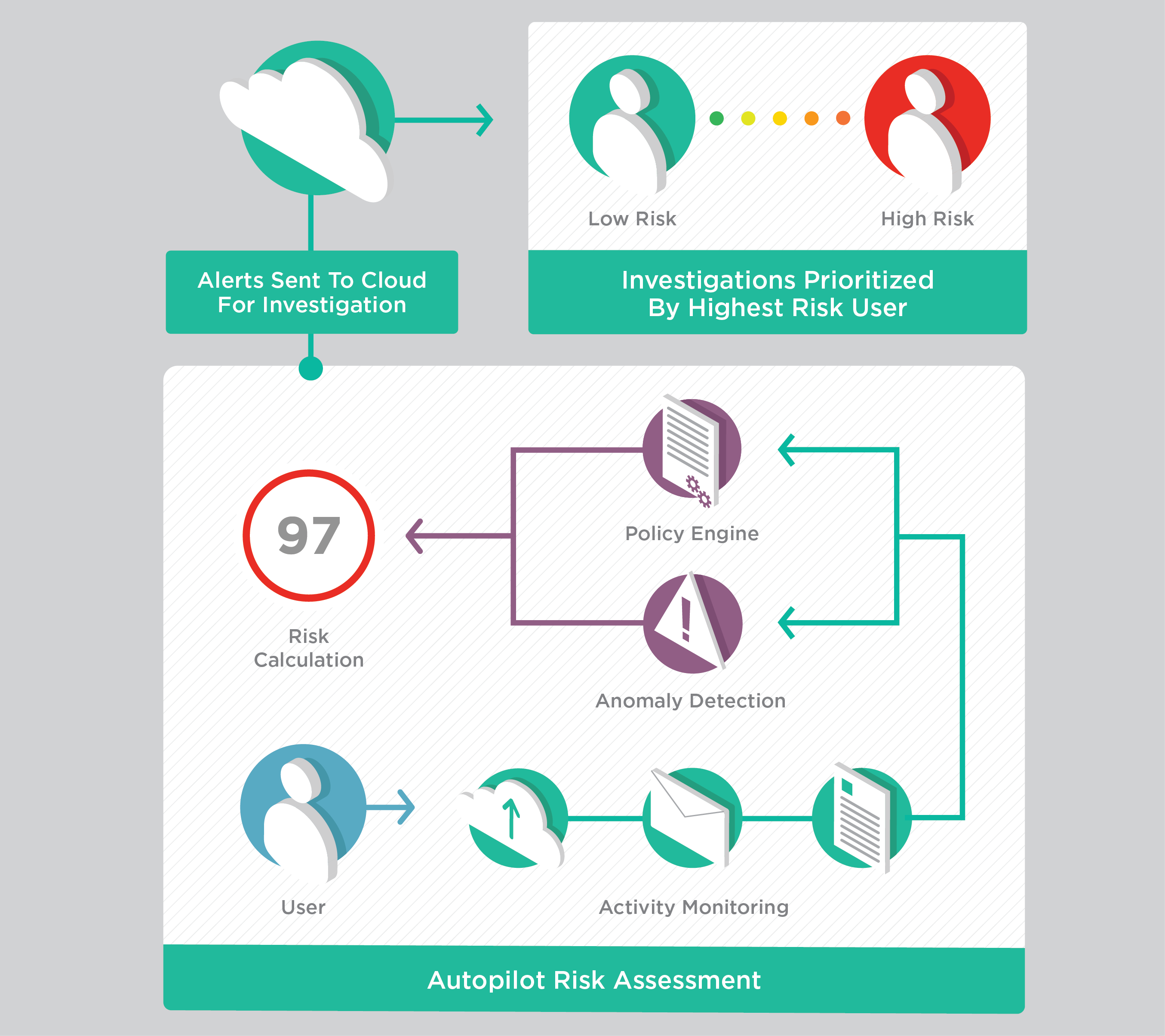
User and Data-Centric Security
Traditional security tends to take an outside-in approach, starting with the perimeter and building layers of security toward the data, all to keep the bad guys out. As many companies started to realize during the Sunburst attack—that’s an approach that falls short. So why not take an inside-out approach instead? Attempts to rein in users and data tend to be counterproductive because they usually cost organizations dearly, both in terms of production and overall efficiency. A user and data-centric security approach no longer starts with where they reside. No longer tethered to a fixed network, unbound employees become liberated from hardware infrastructure limitations of the past.
No matter how robust security strategies are, data breaches will continue to happen. As users continue to work remotely, they’ll continue to introduce new security risks. The cybersecurity path forward requires a deeper analysis of behaviors. The first step is establishing a behavior baseline at the individual level. What constitutes normal behavior? What behavior is unusual? Bad actors impersonate our employees to access and steal our data. Taking a closer look at how users interact with data no matter where it resides will help move the unbound enterprise left of breach. The deep understanding of behavior and risk creates a shift in security strategy—one where policies no longer have to be binary but instead, automatically personalized to the user.
Cloud and Intelligent Security
Due to the level of specialized talent focused on cloud security, overall security of cloud applications often exceeds on-premises application security. But even cloud providers suffer from the talent shortage, and data security is still the responsibility of your organization and the employees accessing data.
And no security team can do it all. These days, you need to leverage AI and machine learning to help with creating and enforcing rules that play a role in executing security strategy at the user level. Done correctly, this marriage between cloud security and AI security will be invisible to the user. Productivity won’t be disrupted. Even better, a truly dynamic system can help identify and react to indicators of behavior, keeping your organization left of breach.
The unbound enterprise will bring new levels of productivity and efficiency to organizations and their employees—but getting there requires a security strategy that is unbound as well. Expect to hear more on this topic from me and from other senior Forcepoint leaders in 2021. Until then, wishing you and your teams a safe and healthy end to this year!

