Today, we’re launching Dynamic User Protection, a product that redefines modern user activity monitoring and insider threat protection. Dynamic User Protection represents a critical component of our converged cloud security platform portfolio moving forward. With Dynamic User Protection, we’re focused on bringing user activity monitoring to a broader range of customers.
The Complete Guide to Insider Risk
The National Counterintelligence and Security Center in the US declared September to be a National Insider Threat Awareness Month. The declaration aims to educate organizations on spotting and reporting insider threats to stay ahead before they manifest into negative outcomes for the organizations, its employees, partners and/or customers. According to Gartner, nearly 75% of data breaches happen due to risky insider behavior or as a result of compromised access. Insider threats are now a perennial security risk to any organizations globally.
The problem stems from the traditional infrastructure-centric security approach to trust everything managed by enterprise IT teams:
- Managed data centers
- Managed devices
- Managed applications
- Managed identities
In the above, managed is a proxy for trust – implicit trust. With the rapid shift to cloud and the new way of working from anywhere using any device, infrastructure-centric security approaches fall short.
Early behavioral analytics and insider threat solutions were designed for the traditional infrastructure-centric security – used by security operations and response teams, applying user-context to primarily traffic-based event logs and looking for the proverbial needle in the haystack.
Modern enterprise networks have now evolved into a highly distributed environment, users working from wherever they are, often bypassing the enterprise infrastructure altogether and leaving the traffic-based analysis with “event blind-spots” to make any meaningful detection on insider threats and risks. In addition, the early adopters of this approach were elite enterprises with a dedicated team of data scientists that were employed to train the artificial intelligence (AI) and machine learning models and manually comb through alerts to piece together a view of how a data breach occurred.
Modern enterprises are now turning to Zero Trust as a security paradigm that replaces implicit trust with continuously assessed explicit risk/trust levels based on context – most notably how users interact with the business data – that adapt to risk-optimize the organization’s security posture.
Here’s a look at traditional security compared to a human-centric approach:
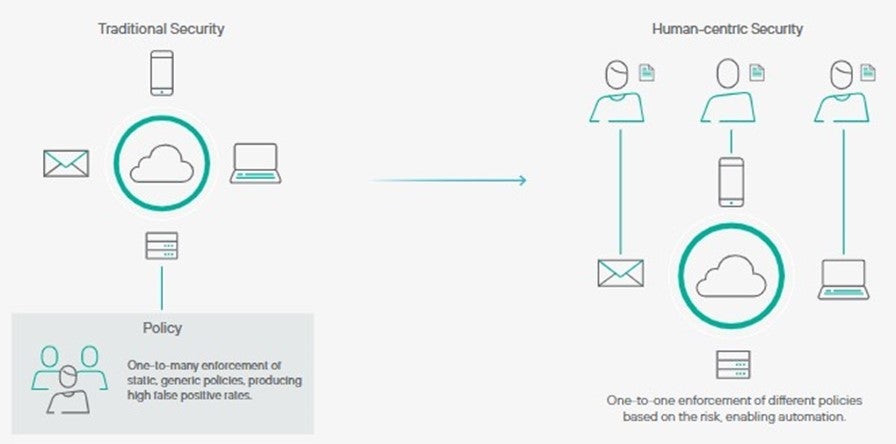
This new user protection approach overcomes these challenges – one designed for a Zero Trust paradigm and a cornerstone of a human-centric cybersecurity strategy. Our cloud-based solution targets humans as the new perimeter, continuously evaluating their interactions with data wherever its used and proactively surfacing observed malicious use, compromised access, data loss risks.
Here’s a visual that illustrates how a user’s actions may impact their overall risk score:
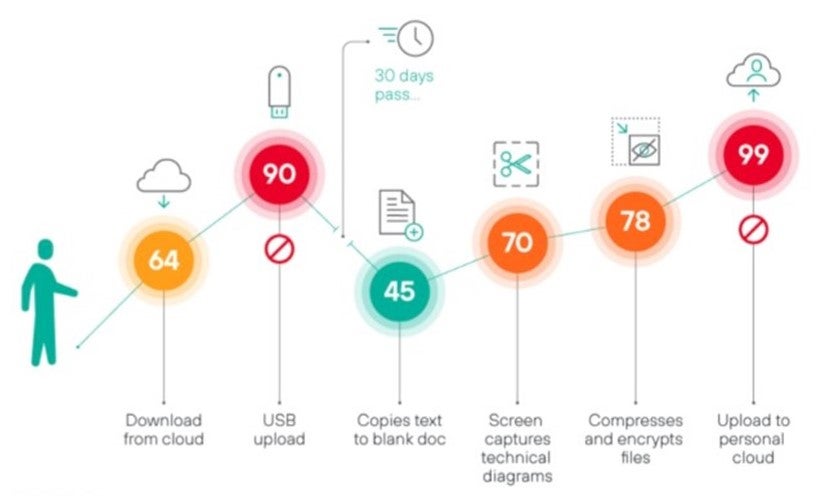 This provides organizations of any size the ability to gain meaningful visibility into risky user behavior at the earliest point of detection (on the endpoint) and to respond to aggregated user risk levels and automatically enforce risk-adaptive data protection.
This provides organizations of any size the ability to gain meaningful visibility into risky user behavior at the earliest point of detection (on the endpoint) and to respond to aggregated user risk levels and automatically enforce risk-adaptive data protection.
If you are a security leader responsible for implementing user protection for the modern enterprise, you should evaluate the approach that will enable you to:
- Get left of loss – gain meaningful visibility into risky user behavior and mitigate loss with a risk-adaptive data protection.
- Ease adoption and deployment – a cloud-based service with highly scalable, distributed endpoint-based analytics for rich on- and off-network risk evaluations that does not require specialized skills to tune any AI/ML models.
- Provide risk-adaptive protection – take action on insider risks and threats and only act based on indicators of behaviors (IoBs) that will expose business critical data and intellectual property.
Forcepoint is dedicated to human-centric cybersecurity, understanding your perimeter is where your people are. By understanding human behavior, we are able to proactively detect risk and secure data and intellectual property.
Today, we’re announcing general availability of Forcepoint Dynamic User Protection to help democratize user activity monitoring with the sole purpose of protecting enterprise users and data against security risks.
In the coming weeks, we’ll continue to publish more posts on topics related to user activity monitoring and Dynamic User Protection.

